This article is intended for Citrix administrators and technical teams only.Non-admin users must contact their company’s Help Desk/IT support team and can refer to CTX297149 for more information How to disable Citrix Receiver from popping up during logon to the Desktop. Open the Citrix Receiver Group Policy Object administrative template by running gpedit.msc. Under the Computer Configuration node, go to Administrative Templates Citrix Components Citrix Receiver DPI Select High DPI policy. Change the settings as required. Use Citrix Receiver to access your applications and desktops. Detect Receiver If you do not want to detect/install Citrix Receiver you can use the light version, with fewer features, in your browser.
Symptoms or Error
How to disable Citrix Receiver from popping up during logon to the Desktop.
Solution
Disabling Startup Programs in Windows 7, Vista, or XP
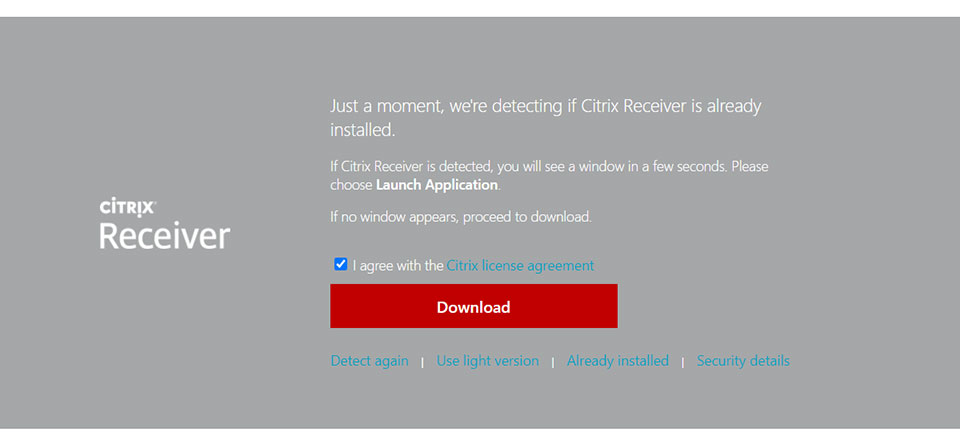
Citrix Receiver Light Version


For some programs, it’s smart to have them start with Windows, such as anti-virus and firewall software. However, for most programs, starting them at boot-up just wastes resources and extends startup time. There is a tool installed with Windows, called MSConfig, that allows you to quickly and easily see what’s running at startup and disable the programs you prefer to run on our own after startup as needed. This tool is available and can be used to disable startup programs in Windows 7, Vista, and XP.
NOTE: MSConfig can be used to configure several things other than just startup programs, so be careful what you do with it. If you’re not sure about using it, just follow the steps in this article and you should be fine.
To run MSConfig, open the Start menu and type “msconfig.exe” (without the quotes) in the Search box. As you type, results display. When you see “msconfig.exe,” click on it or press Enter, if it is highlighted.
NOTE: If you are using Windows XP, open the Run dialog box from the Start menu, type “msconfig.exe” in the Open edit box, and click OK.
What Is Citrix Receiver
Click the Startup tab on the System Configuration main window. A list of all the startup programs displays with a check box next to each one. To prevent receiver from starting up with Windows, select the check box next to the Citrix Receiver so there is NO check mark in the box. Click OK once you have made your choices.
A dialog box displays telling you that you may need to restart your computer for the changes to take affect. Click Restart to restart your computer immediately. If are not ready to restart your computer, click Exit without restart.
Ms office educational discount.
Disabling Startup Programs in Windows 8 or 8.1 or 10
Windows 8, 8.1, and 10 make it really simple to disable startup applications. All you have to do is open up Task Manager by right-clicking on the Taskbar, or using the CTRL + SHIFT + ESC shortcut key, clicking “More Details,” switching to the Startup tab, and then using the Disable button.
For Windows Server OS - locate the startup folder using 'shell:common startup' command in Run.
Additional resource-
Suppressing Add Account dialog
https://docs.citrix.com/en-us/citrix-workspace-app-for-windows/getting-started.html#user-accounts
When Workspace App for HTML5 is hosted on a https site (default and recommended), non SSL/TLS websocket connections are prohibited by browsers.
In explaining the technical reason behind this it is important to understand the following two principles:
1. Western dresses sketches designs. As opposed to existing as a separate process, Citrix Workspace App for HTML5 operates within the frame and process space of the browser itself. As such the browser has the ability to enforce certain security parameters.
This second point is less obvious in the case of Citrix Workspace App for HTML5 because the published desktop or application displays within the browser frame and “appears” to be connected via the Storefront server. Despite this appearance though, the underlying TCP/UDP connection is still between the client and the VDA. If the Storefront base URL is SSL enabled (where it begins with https as is best practice) and the VDA is not SSL enabled (which it is not by default) the browser in this case will prevent the connection due to what it sees as an underlying inconsistency. The inconsistency is that while the URL shown in the browser frame is prefixed with https, the actual underlying connection is not https even though it is not obvious to the user.
There are two solutions for this.
Solution 1 is to enable SSL on the VDA using the following guide:
This will ensure that the connection path is SSL enabled between the internal client and the VDA.
 Solution 2 is to have your connections from the clients first go through a Citrix Gateway. Citrix Gateway will proxy the connections and perform a SSL handshake between the client and the Citrix Gateway. In this scenario there is no inconsistency and connections via HTML5 Receiver will succeed.
Solution 2 is to have your connections from the clients first go through a Citrix Gateway. Citrix Gateway will proxy the connections and perform a SSL handshake between the client and the Citrix Gateway. In this scenario there is no inconsistency and connections via HTML5 Receiver will succeed.Additional Resources
